Challenges & Objectives
Due to complex nature of modern production environments, the facilities often encompass vast areas with multiple entry points, making it difficult to monitor and control access effectively
- Security Assessment: Security is sometimes an afterthought, lacking a consistent, defined strategy.
- Security Awareness: Engaging employees and changing behaviors remains a challenge
- Unsecured Networks: A Gateway to Factory Assets Unsecured networks provide attackers access to factory systems and data.
- Unpatched Vulnerabilities : Attackers may easily exploit known security weaknesses in ICS systems. Insecure remote access systems, vulnerable software or even outdated legacy equipment or software, are an attacker’s paradise.
- Physical Access: Open Doors to Digital Vulnerabilities Physical entry points make substations vulnerable to attacks. By breaking in or using social engineering, attackers can access crucial systems.
- Securing manufacturing environments involves collaboration, risk assessment, and ongoing vigilance.
- Regular security training, awareness campaigns, and clear policies helps educating employees about security best practices fosters a safer work environment and protects valuable assets.
- Prioritize network security by using robust encryption protocols and firewalls, and routinely monitoring network traffic for suspicious activities.
- Timely patch management, Blocking unauthorized remote access and vulnerability screening reduce vulnerability risk.
- Controls, surveillance, and security should prohibit unauthorized physical access to important locations.

Project Proposal
Zealinx services is a service-based startup company based in Trichy, India. We specialize in Cyber security and Engineering solutions for Operational Technology industries, Improving Digitalization.

Assess
Formulate the production process, data flow, Analyze the assets involved on criticality and business impact, Understand the site situation and perform risk analysis and Internal Audit.
- Security fingerprint (manual asset inventory)
- High level criticality assessment
- System under consideration- Define zones and
conduits - High-level network overview – Current setup
- Data flow diagram
- Process flow diagram
- Risk assessment on zone level
- Internal Audit
- Mitigation plan
- Gap analysis

Design
Assign the site security responsible, give awareness to the site employees, Analyze the gap identified on audit and design the recommended action to implement.
- Define IT and OT representatives for the site
- Providing Security awareness Training for site
employees - Define Procedures to follow the process
- Defining requirements based on gap analysis
- Pilot Project Proposal
- Define PoC & PoV
- Technology proposal
- Defining Network segmentation with respect to
zones and conduits. - Defining standard IP with subnet allocation for zones
- Client approval on proposal
- Cyber security Topology Design
- Basic conceptual & Detail Design overview

Implement
Leverage technology tools to implement cyber-physical security measures at the site, governing the manufacturing processes.
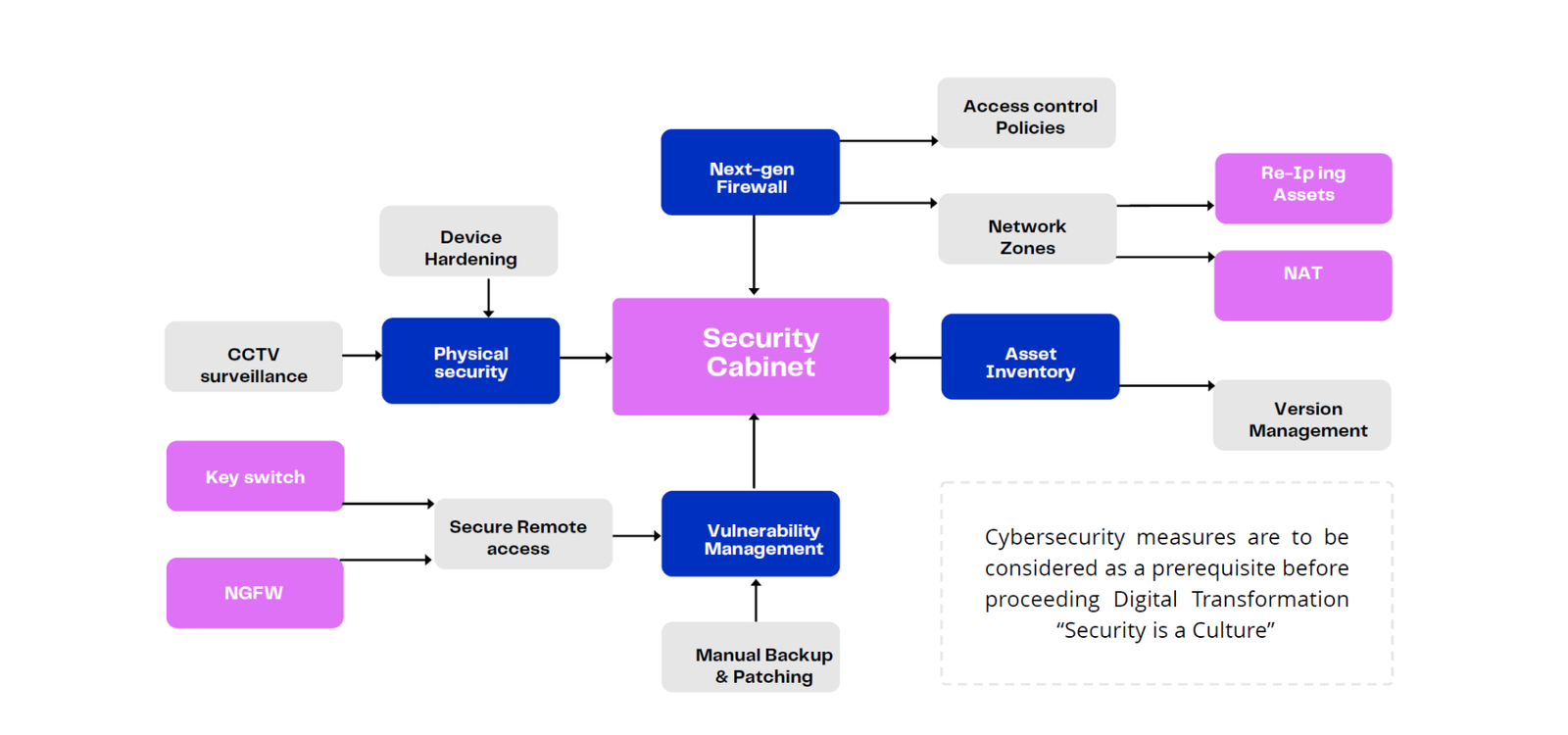
- Implementing IP change in existing systems without
maximum interruption of process - Implementing IT/ OT Next-Gen Firewall (Palo
Alto/Fortigate) - Implementing File storage server & Syslog collector
(syslog-ng) - Implementing Backup & Recovery (Acronis)
- Implementing Vulnerability & Asset management
systems (OT Base) - Implementing Device hardening & Patch management
- Implementing Version Management System (Octoplant)
- Implementing Secure Remote Access system (Talk2MEwon)
- Implementing Access Control System for cabinets or
doors (Honeywell)
Security Surveillance System Integration (Honeywell &
AnnexSECURE)
Securing the Future of Industrial Operations with Advanced OT Cybersecurity

Target
Manufacturing factories, Energy sectors

Technology
Security Risk portfolio, Policies and Device hardening

Team
IT Engineer, OT Engineer, Project Manger

Reason
Enable Digitalization and Industry 4.0
Standards
Adopting international standards and best practices to enhance security, we undergo the following standards.
Brainstorm
Securing the Future of Industrial Operations with Advanced OT Cybersecurity
cybersecurity should be an integral part of any digital transformation initiative to safeguard data, operations, and overall resilience.
know your Assets involved on operations
Improve convergence between IT and OT resources
SOLUTION - TIMELINE
In the realm of project development, Proof of Concept (PoC) and Proof of Value (PoV) are critical stages that serve as milestones in the innovation journey. A PoC is typically the initial phase where the technical feasibility of an idea is tested, answering the fundamental question of whether the concept can be transformed into a working model. Following the successful demonstration of a PoC, the PoV phase commences to assess the practical value and potential return on investment of the concept when implemented on a larger scale.
PHASE 1
RISK ANALYSIS
Risk analysis is a vital process that involves identifying potential threats and vulnerabilities, assessing the likelihood of threat occurrence, and evaluating the potential consequences in operation.
PHASE 2
AWARENESS
Security awareness is paramount, especially in an era where the threat landscape is rapidly evolving.
PHASE 3
PoC & PoV -PILOT
The focus on minimum security and resilience requirements highlights the shift from a voluntary approach to a more structured and mandatory framework to address the complex, interconnected threats faced today. This strategic approach is designed to enhance the resilience and security of critical infrastructure.

Project Delivery
- Cybersecurity Assessment Report- Asset Inventory report, High level Network Diagram, Process flow Diagram, Data flow Diagram, Audit Report, Recommendation document to mitigate risks.
- Cybersecurity Awareness Report- Security awareness training material delivery , Recommended Network segmentation on zone level, Change management process document, Manual Patching procedure, Manual backup & recovery procedure.
- Cybersecurity Implementation: Cabinet delivery with 3 Physical Hardware with Vmware Esxi host and Virtual Machines: Virtual Next-Gen FW, File storage server, Syslog server, Version Management, Asset management, Ixon cloud - IX Router device (Remote access solution), Backup of OT devices (4 times per year) and Vulnerability assessment (Once a Year).
- Surveillance Implementation: CCTV Cameras, NDR, IX router, Video Management system integration
- Device Hardening- USB lockers and Ethernet Port lockers for Systems and Network components.
- Central management surveillance operation (AXIS Communication)
ROI
- Empower modern working methods for internal employees:
- Remote work (home and office)
- Site and regional collaboration to provide common solutions
- Maintain security and foster creativity
- Modernize working methods with vendors and solutions
- Reliable and secure remote access
- Industry 4.0 and cloud integration (Predictive maintenance, Augmented reality)
- Simplified IT/OT integrations, governance, and digitalization initiatives
- Historian and other MES
- Scalable IT and OT integrations
- Visibility and standard protocol usage

Comprehensive OT Cybersecurity Services
Our services include comprehensive OT security audits, real-time threat monitoring, risk assessment and management, incident response, and compliance training, all tailored to protect and optimize industrial control systems and critical infrastructure.

Security Ess
Critically assessment, Risk assessment, Internal Audit, Gap Analysis, Crafting Standards

Security Pro
Security Ess + High level network design, security awareness, crafting policies & procedures

Security Adv
Security Pro + Next-Gen FW, Asset inventory, Version Management, vulnerability, Patch & Backup Management, Secure Remote access

Security Phy
CCTV Surveillance System, Access control systems, Device hardening

