Cyber Engineering: Strategies for a Secure Feeling
In today’s digital landscape, the need for robust cyber engineering solutions is paramount. At Zealinx, we specialize in comprehensive cyber engineering services designed to protect your systems, enhance your infrastructure, and ensure your operations run smoothly. Whether you're in India, the US, Europe, or the UK, our tailored solutions are here to meet your unique needs.
What is Cyber Engineering?
Cyber engineering refers to the application of engineering principles to design, build, and maintain secure systems. This involves integrating cybersecurity measures into every phase of system development and operation. At Zealinx, our services ensure that your organization is not only compliant with industry standards but also resilient against evolving cyber threats.

High Level System Architecture
Our team excels in developing High Level System Architecture tailored to your organization's objectives. By analyzing your current infrastructure and future goals, we create a strategic framework that aligns technology with your business vision. This ensures a resilient and adaptable cyber environment.
1. Enhanced Security: A well-designed architecture minimizes vulnerabilities and provides robust defenses against cyber threats.
2. Scalability: As your business grows, your systems can be easily scaled to accommodate new demands without compromising security.
3. Cost Efficiency: By optimizing your architecture, we help you reduce unnecessary expenses and maximize your IT investments.

Network Segmentation
Network Segmentation is essential for minimizing vulnerabilities. We implement effective segmentation strategies that isolate critical assets and reduce the attack surface, ensuring that a breach in one area doesn't compromise your entire network. Our experts guide you in structuring your network for maximum security.
1. Asset Identification: We begin by identifying your critical assets and understanding their interconnections.
2. Segment Design: Based on your infrastructure, we design logical segments that enhance security while maintaining operational efficiency.
3. Monitoring and Management: Continuous monitoring of segmented networks ensures that potential threats are identified and addressed swiftly.

Next-Gen Firewall Implementation
Upgrade your defense mechanisms with our Next-Gen Firewall Implementation services. We deploy advanced firewalls equipped with AI and machine learning capabilities, enabling real-time threat detection and response. Protect your data and maintain compliance with our cutting-edge solutions.
1. Deep Packet Inspection: Analyze data packets thoroughly for threats.
2. Intrusion Prevention Systems (IPS): Identify and block malicious traffic before it enters your network.
3. Application Awareness: Control traffic based on applications, enhancing security policies.

Secure Remote Access
In an era of remote work, ensuring secure connections is crucial. Our Secure Remote Access solutions provide your team with safe, reliable access to your systems from anywhere in the world. We utilize strong encryption protocols to safeguard your data against unauthorized access.
1. Multi-Factor Authentication (MFA): Enhance security by requiring multiple verification methods.
2. Virtual Private Network (VPN): Create secure tunnels for data transmission, protecting sensitive information.
3. Access Control Policies: Define who can access what, minimizing potential risks.

OT Backup Management
Operational Technology (OT) is vital for many industries, and our OT Backup Management services ensure your critical systems remain operational even in emergencies. We create robust backup strategies that protect your data and minimize downtime.
1. Assessment: Evaluate your current backup processes and identify gaps.
2. Strategy Development: Create a tailored backup plan that meets your operational needs.
3. Testing and Implementation: Regularly test backup solutions to ensure reliability during a crisis.

Device Hardening
Enhance the security of your devices with our Device Hardening services. We systematically strengthen your hardware and software configurations, ensuring that your systems are resilient against cyber threats. Our team implements best practices tailored to your specific environment.
1. Patch Management: Regularly update software to fix vulnerabilities.
2. Configuration Management: Apply security configurations that reduce attack surfaces.
3. User Access Controls: Limit user permissions based on roles to minimize risks.
Cyber Security Engineering: A Comprehensive Approach
Cybersecurity engineering encompasses the practices, policies, and technologies designed to protect an organization’s information systems. Our approach is holistic, integrating risk assessment, threat modeling, and incident response into every aspect of your cybersecurity strategy.
- 1. Risk Assessment: Identify vulnerabilities and assess the potential impact on your organization.
2. Threat Modeling: analyze potential threats and develop strategies to mitigate risks.
3. Incident Response Planning: Create a detailed response plan to address security breaches effectively.
Proven Success and Satisfied Clients
At Zealinx, our track record speaks for itself. We have successfully transformed security infrastructures for a diverse range of clients, enhancing their operational resilience and ensuring peace of mind. Our commitment to excellence and customer satisfaction sets us apart in the cyber engineering landscape.
In competitive business landscape, efficiency and innovation are essential. To stay ahead of the curve, organizations must utilize cutting-edge technology to automate their processes and enhance operations and better serve their clients.
Our Cyber Engineering Services in Operational Technology tackle this very issue by leveraging digital transformation techniques for a smoother, safer, and more innovative approach to business operations.
Many of our clients have attested to our exceptional service: "Our experience with the Cyber Engineering Services in Operational Technology has been nothing short of exceptional. They've transformed our network safety and have significantly improved our theft management and production processes"
Transform Your OT Network Today—Get Started Now
Are you ready to elevate your cybersecurity posture? Transform your OT network with our expert cyber engineering services.
Get in Touch Today!
Contact Us



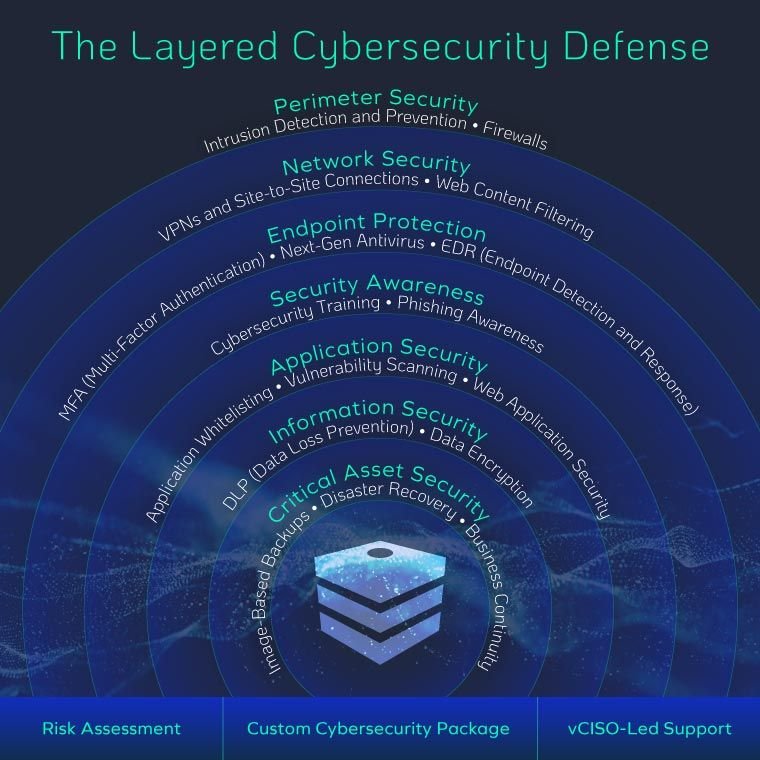
Designing Security Into Every Layer of Your Infrastructure
Cyber engineering is a specialized discipline that blends cybersecurity, systems engineering, and software integration to build secure, resilient digital environments. It focuses on embedding security into every layer of your infrastructure—from hardware and software to networks and data systems—ensuring systems are secure by design, not by afterthought.
At Zealinx, we recognize the critical importance of building secure digital ecosystems from the ground up. Cyber engineering is not just a component—it's the foundation. By integrating principles from cybersecurity, systems engineering, and software development, we ensure every layer of infrastructure is fortified against emerging threats. This proactive approach embeds security into hardware, software, networks, and data systems, resulting in solutions that are robust, resilient, and trusted.
How confident are you that your systems are secure by design?
Zealinx designs secure systems using the Purdue Model and ISA/IEC 62443, ensuring layered protection and resilience from IT to OT.

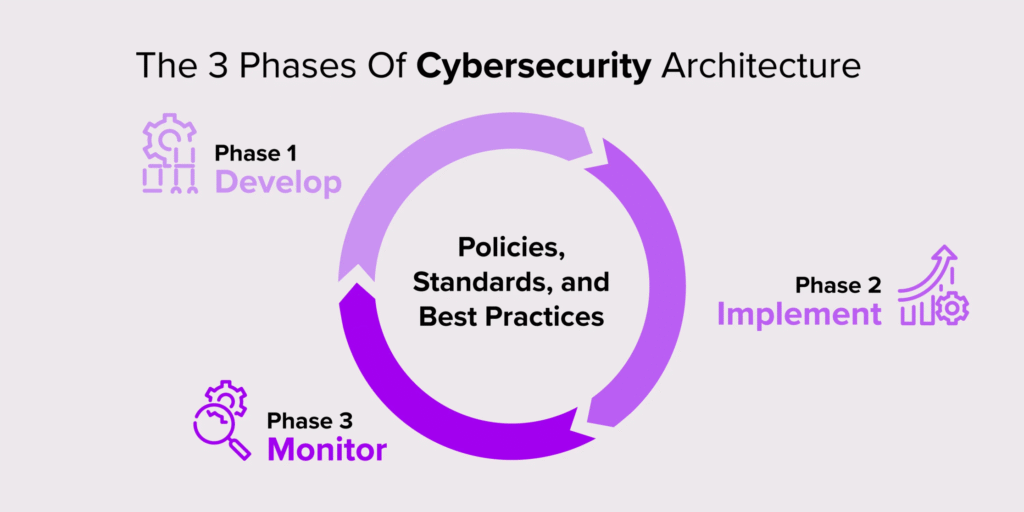


Security Architecture & Design
We plan and integrate secure infrastructure based on customer-defined requirements. This includes designing network structures, defining zones and conduits, assigning IP schemes, recommending communication protocols, and planning physical layouts like cabling and equipment placement. We adopt and securely integrate vendor technologies into a cohesive, standards-aligned architecture—ensuring your systems are scalable, compliant, and secure by design.


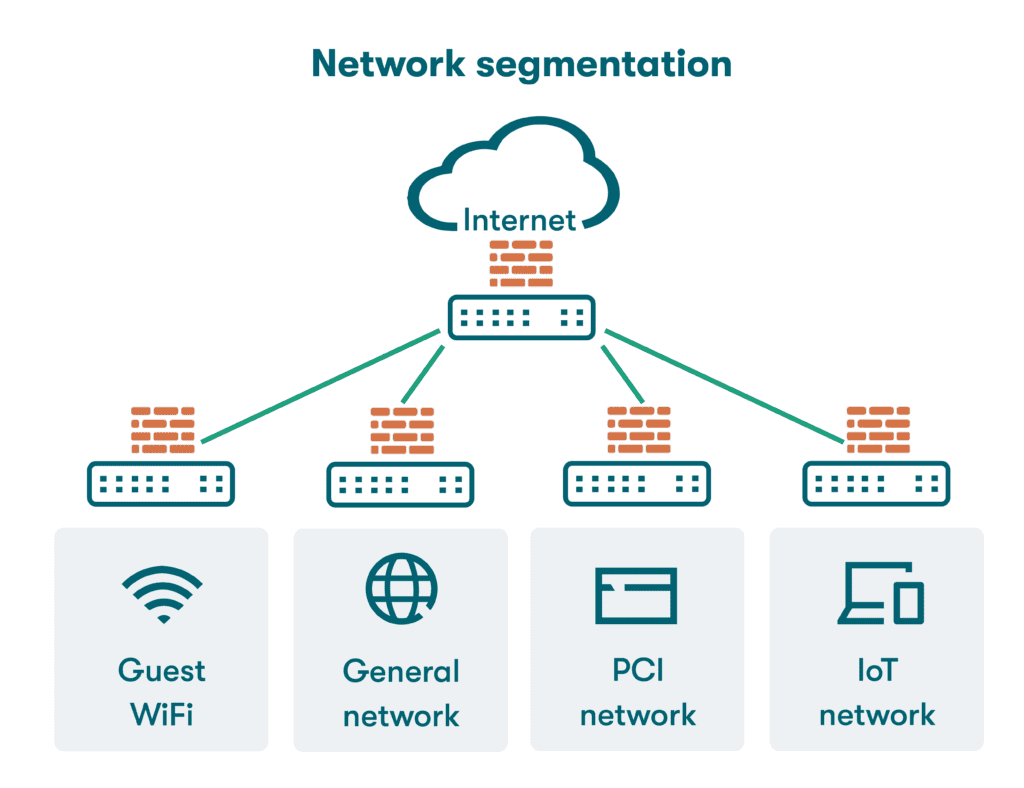
Network Segmentation
We enhance cybersecurity by dividing networks into well-defined zones and conduits, limiting lateral movement and improving control over data flows. Our team defines trusted zones, configures inter-zone conduits, and implements VLANs, firewall rules, and ACLs. We also provide IP plans and integrate intrusion detection systems to isolate threats and support compliance with IEC 62443 and NIST.



Secure Remote Access
We securely integrate vendor-provided remote access solutions tailored to your environment. This includes VPNs, secure gateways, MFA, and access policies. We define user roles, configure secure conduits, and implement monitoring tools to ensure safe, compliant, and traceable remote connectivity—supporting operational continuity without compromising security.
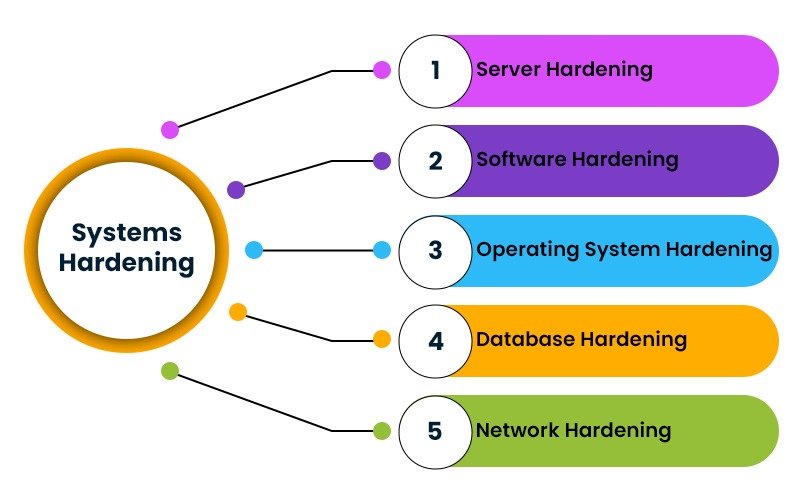

Device Hardening
We configure vendor-supplied devices—PLCs, HMIs, servers, and switches—according to best practices. This includes disabling unused services, enforcing strong authentication, applying secure configurations, and enabling encrypted protocols. Our hardening process aligns with your system design and standards like IEC 62443, reducing the attack surface and ensuring secure device operation.
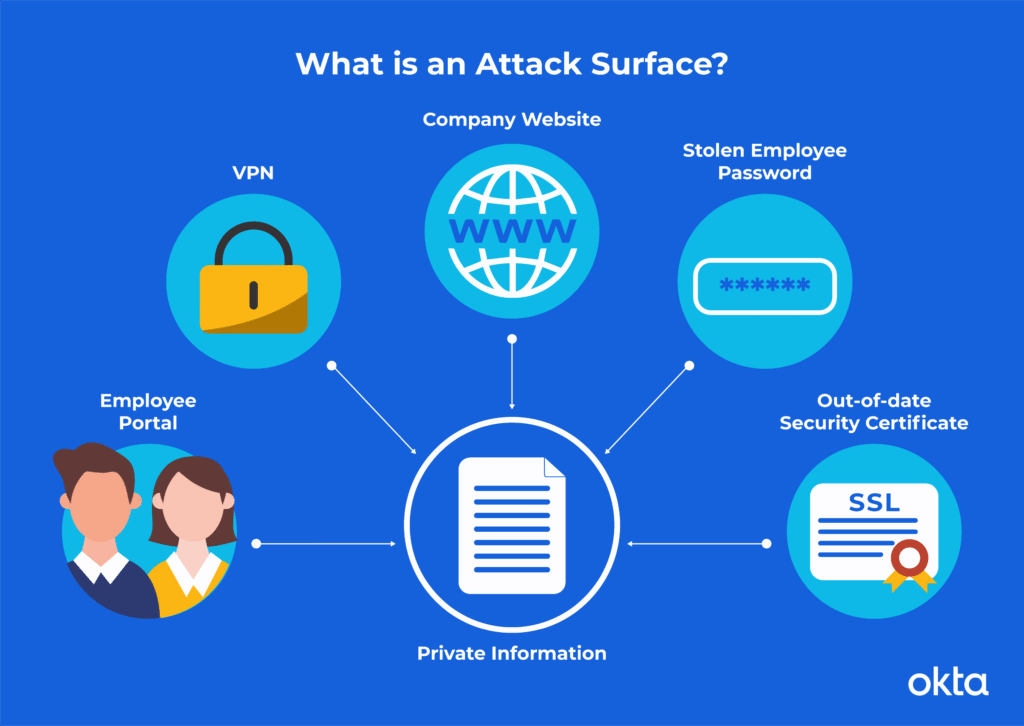
Minimize attack surfaces and prevent lateral movement through layered security.
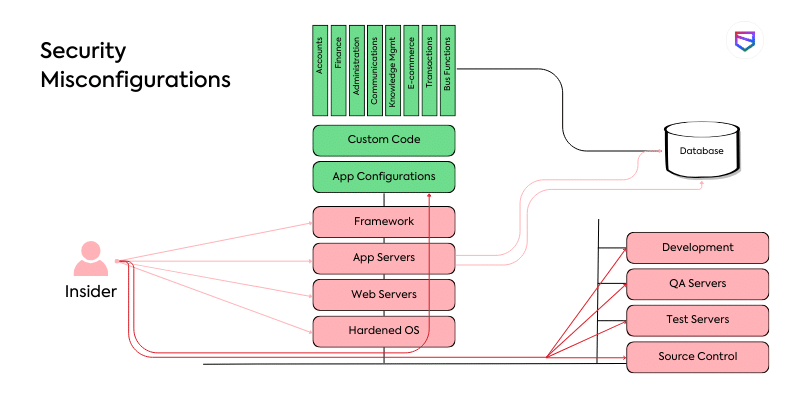
Secure configurations and architectures reduce wear from cyber threats and misconfigurations.
Why Zealinx
Built on Standards. Secured for the Future
We specialize in securely integrating vendor technologies into customer-defined architectures. Our engineering practices align with globally recognized standards like IEC 62443, ISO 27001, and NIST. We ensure your infrastructure is not only secure but also audit-ready and future-proof.
Real-World Configuration. End-to-End Protection.
Our team brings hands-on experience in configuring real-world systems—assigning IP schemes, defining zones and conduits, hardening devices, and implementing secure access—ensuring every layer of your infrastructure is protected.
Partnering for Aligned, Secure Solutions
We work closely with your internal teams, aligning our services with your design, operational goals, and compliance needs. You stay in control—we enhance and secure what you’ve built.
Proactive Engineering for Long-Term Value
Our services reduce long-term operational risks, lower incident response costs, and improve system resilience—delivering measurable ROI through proactive engineering.


FREQUENTLY ASKED QUESTIONS
1. What does Zealinx’s high-level system architecture service include?
We design and implement resilient network architectures tailored to your needs, ensuring maximum uptime and optimal performance for your critical systems.
2. How does Zealinx’s network segmentation enhance security?
Our network segmentation creates strong boundaries within your OT infrastructure, limiting unauthorized access and minimizing the impact of security breaches.
3. What are the benefits of implementing a Next-Gen Firewall (NGFW) with Zealinx?
NGFWs protect your OT infrastructure from emerging threats by providing comprehensive security against unauthorized access and maintaining system integrity.
4. How does Zealinx ensure secure remote access to OT networks?
We provide secure remote access solutions that allow employees to connect to OT networks safely from any location, enhancing productivity while safeguarding your infrastructure.
5. What does Zealinx’s OT backup management service involve?
We implement robust backup strategies, automate backups, and regularly test restore capabilities to ensure quick recovery from system failures, errors, or cyber attacks.

